1、身份鉴别
1.1 密码复杂度,长度设置和错误次数
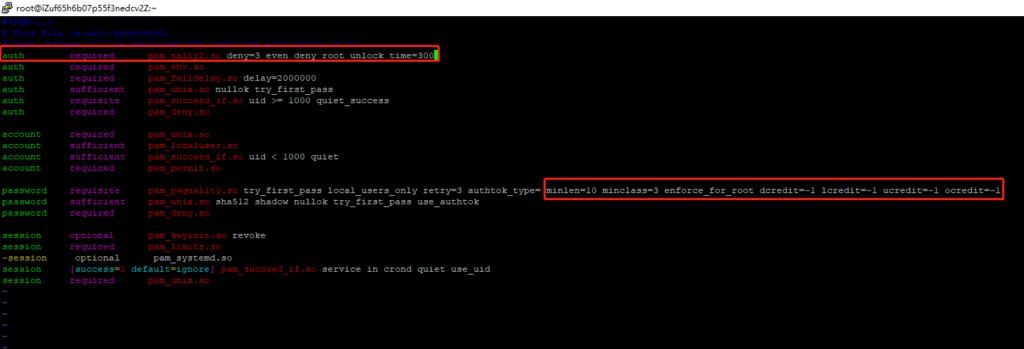
使用vim /etc/pam.d/system-auth打开配置文件进行编辑,在pam_cracklib.so或pam_pwquality.so所在行末尾追加:minlen=10 minclass=3 enforce_for_root dcredit=-1 lcredit=-1 ucredit=-1 ocredit=-1;并且在首行添加:auth required pam_tally2.so deny=3 even_deny_root unlock_time=300
1.2 设置密码有效期
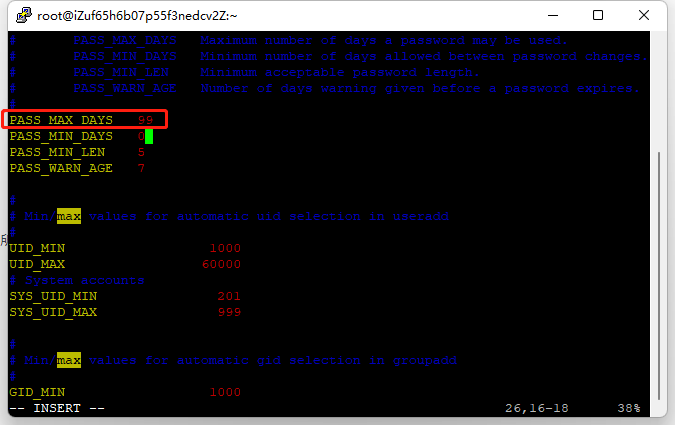
使用vim /etc/login.defs打开配置文件,修改配置文件中的PASS_MAX_DAYS 设置成指定日期。
对于已经存在的账号,使用命令手动进行调整:
[root@iZuf65h6b07p55f3nedcv2Z ~]# grep -v '!' /etc/shadow|grep -v '*'
root:$6$m/lHH/etxN8uxs$7KjQ4qRv79AGcZOsFO6RN/FqqM7GPqTpkKdGKPYwn4CDmkwKnQyMQYv/0An0XJHkW8nra2DaZdwcRNeEbTjR1/:19317:0:99999:7:::
[root@iZuf65h6b07p55f3nedcv2Z ~]# chage -M 99 root
[root@iZuf65h6b07p55f3nedcv2Z ~]# grep -v '!' /etc/shadow|grep -v '*'
root:$6$m/lHH/etxN8uxs$7KjQ4qRv79AGcZOsFO6RN/FqqM7GPqTpkKdGKPYwn4CDmkwKnQyMQYv/0An0XJHkW8nra2DaZdwcRNeEbTjR1/:19317:0:99:7:::1.3 登录错误锁定设置
使用vim /etc/pam.d/password-auth命令打开配置文件,在首行添加auth required pam_tally2.so deny=3 even_deny_root unlock_time=300
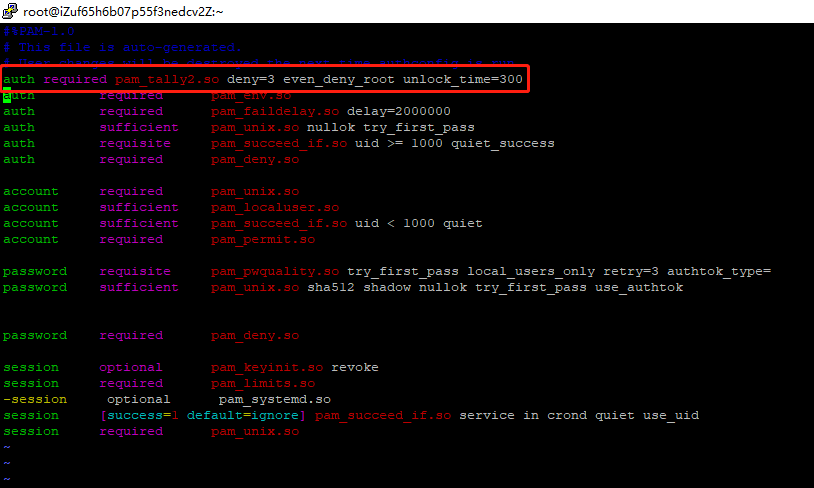
说明:如为CentOS 8或Euler OS,则应将pam_tally2.so替换为pam_faillock.so
1.4 空闲超时自动退出
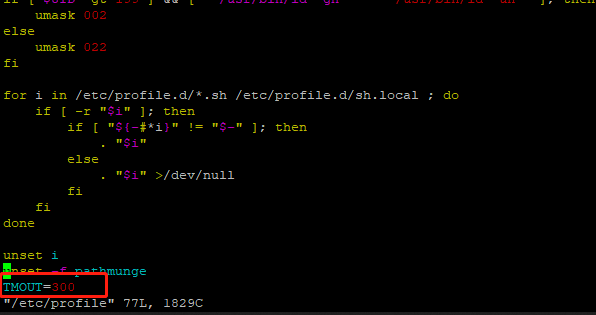
使用vim /etc/profile打开配置文件,在文件末尾添加TMOUT=300,保存退出后,使用source /etc/profile使配置生效。
2、访问控制
2.1 禁止root进行登录
首先创建登录账号进行使用(如果已经有对应账号,则直接到设置步骤)。
[root@iZuf65h6b07p55f3nedcv2Z ~]# adduser java
[root@iZuf65h6b07p55f3nedcv2Z ~]# passwd java
New password:
Retype new password:
passwd: all authentication tokens updated successfully.
[root@iZuf65h6b07p55f3nedcv2Z ~]# chmod -v u+w /etc/sudoers
[root@iZuf65h6b07p55f3nedcv2Z ~]# vim /etc/sudoers在文件中找到root ALL=(ALL) ALL,然后添加java ALL=(ALL) ALL(java为对应创建的用户名称)

编辑完成后,将sudoers权限关掉。
[root@iZuf65h6b07p55f3nedcv2Z ~]# chmod -v u-w /etc/sudoers
mode of ‘/etc/sudoers’ changed from 0640 (rw-r-----) to 0440 (r--r-----)拥有用户过后,就可以禁止root账号了。使用sudo vim /etc/ssh/sshd_config打开配置文件,将【#PermitRootLogin yes】改为【PermitRootLogin no】。
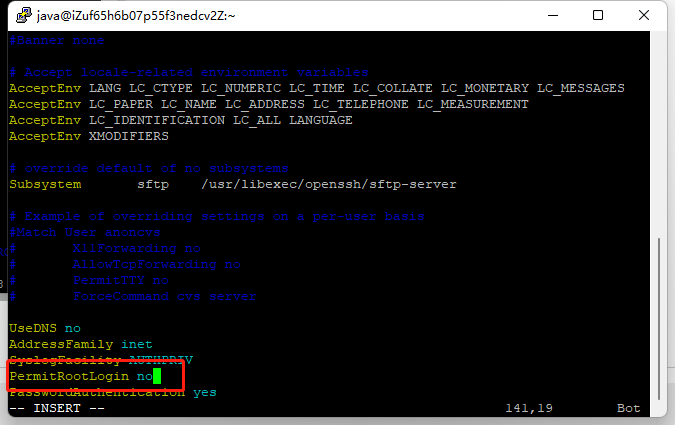
使用sudo systemctl restart sshd重启服务,让配置生效。
2.2 设置三权分立账号
添加系统管理员账户sysadmin、审计管理员账户audadmin、安全管理员账户secadmin。添加方法见2.1
2.3 生成登录密钥文件
调用命令生成密钥文件,命令如下:
[java@iZuf65h6b07p55f3nedcv2Z ~]$ ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/home/java/.ssh/id_rsa):
Created directory '/home/java/.ssh'.
Enter passphrase (empty for no passphrase): 输入rsa密钥密码
Enter same passphrase again:
Your identification has been saved in /home/java/.ssh/id_rsa.
Your public key has been saved in /home/java/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:fuqZgbsiSkWgjkMNbjTg7bFTdabLRRpPgSaatpHq/88 java@iZuf65h6b07p55f3nedcv2Z
The key's randomart image is:
+---[RSA 2048]----+
|o= o.*. |
|= * ..oX |
|.= =+.oo o |
|= o*+ . o |
|o.o=o oS |
| o... o |
|.. . o . |
|... . .. * |
|...o.o+E= |
+----[SHA256]-----+
[java@iZuf65h6b07p55f3nedcv2Z ~]$ ll ~/.ssh/
total 8
-rw------- 1 java java 1679 Nov 21 19:07 id_rsa
-rw-r--r-- 1 java java 410 Nov 21 19:07 id_rsa.pub
[java@iZuf65h6b07p55f3nedcv2Z ~]$ cd ~/.ssh/
[java@iZuf65h6b07p55f3nedcv2Z .ssh]$ cat id_rsa.pub >> authorized_keys
[java@iZuf65h6b07p55f3nedcv2Z .ssh]$ chmod 600 authorized_keys
[java@iZuf65h6b07p55f3nedcv2Z .ssh]$ chmod 700 ~/.ssh/
运行命令sudo vi /etc/ssh/sshd_config,打开密钥登录功能(将PubkeyAuthentication yes前的#去掉):

下载~/.ssh/id_rsa文件到本地,然后执行sudo systemctl restart sshd命令重启服务,使用密钥文件进行登录,验证登录功能是否可用。如果可用,继续修改sudo vi /etc/ssh/sshd_config配置文件:
# sshd不允许空密码登录
PermitEmptyPasswords no
# 禁止密码登录
PasswordAuthentication no重启sshd服务即可。
2.4 修改ssh端口号
执行sudo vi /etc/ssh/sshd_config打开配置文件,修改Port值:
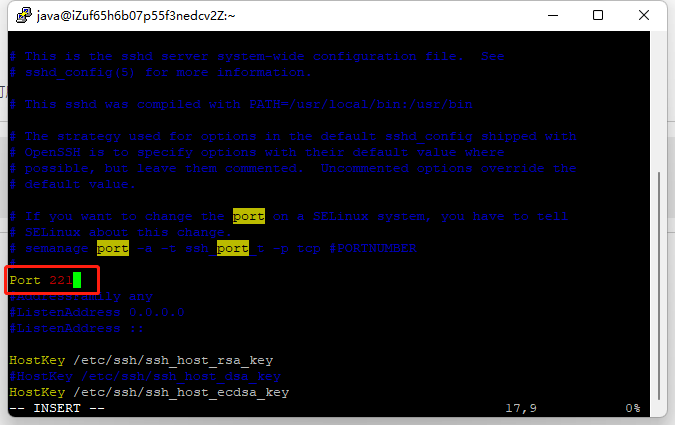
打开防火墙对应的端口,然后重启。
[java@iZuf65h6b07p55f3nedcv2Z ~]$ systemctl status firewalld
● firewalld.service - firewalld - dynamic firewall daemon
Loaded: loaded (/usr/lib/systemd/system/firewalld.service; enabled; vendor preset: enabled)
Active: active (running) since Mon 2022-11-21 19:42:46 CST; 5s ago
Docs: man:firewalld(1)
Main PID: 13166 (firewalld)
CGroup: /system.slice/firewalld.service
└─13166 /usr/bin/python2 -Es /usr/sbin/firewalld --nofork --nopid
[java@iZuf65h6b07p55f3nedcv2Z ~]$ sudo firewall-cmd --zone=public --add-port=221/tcp --permanent
success
[java@iZuf65h6b07p55f3nedcv2Z ~]$ sudo firewall-cmd --reload
success
[java@iZuf65h6b07p55f3nedcv2Z ~]$ sudo firewall-cmd --list-ports
221/tcp
说明(防火墙开机自启):
[java@iZuf65h6b07p55f3nedcv2Z ~]$ sudo systemctl enable firewalld.service
Created symlink from /etc/systemd/system/dbus-org.fedoraproject.FirewallD1.service to /usr/lib/systemd/system/firewalld.service.
Created symlink from /etc/systemd/system/multi-user.target.wants/firewalld.service to /usr/lib/systemd/system/firewalld.service.
[java@iZuf65h6b07p55f3nedcv2Z ~]$ sudo systemctl start firewalld
3、安全防护
3.1 设置审核策略
查看auditd运行状态,确保auditd处于运作中。
[java@iZuf65h6b07p55f3nedcv2Z ~]$ systemctl status auditd
● auditd.service - Security Auditing Service
Loaded: loaded (/usr/lib/systemd/system/auditd.service; enabled; vendor preset: enabled)
Active: active (running) since Mon 2022-11-21 15:04:55 CST; 3h 53min ago
Docs: man:auditd(8)
https://github.com/linux-audit/audit-documentation
Main PID: 462 (auditd)
CGroup: /system.slice/auditd.service
└─462 /sbin/auditd
Warning: Journal has been rotated since unit was started. Log output is incomplete or unavailable.添加审计功能:
[java@iZuf65h6b07p55f3nedcv2Z ~]$ sudo auditctl -w /etc/passwd -p rwxa
[java@iZuf65h6b07p55f3nedcv2Z ~]$ sudo auditctl -w /etc/profile -p rwxa
[java@iZuf65h6b07p55f3nedcv2Z ~]$ sudo auditctl -w /etc/sysctl.conf -p rwxa
[java@iZuf65h6b07p55f3nedcv2Z ~]$ sudo auditctl -w /etc/crontab -p rwxa3.2 日志保存至少6个月
使用sudo vim /etc/logrotate.conf命令打开配置文件,然后将rotate改为26:

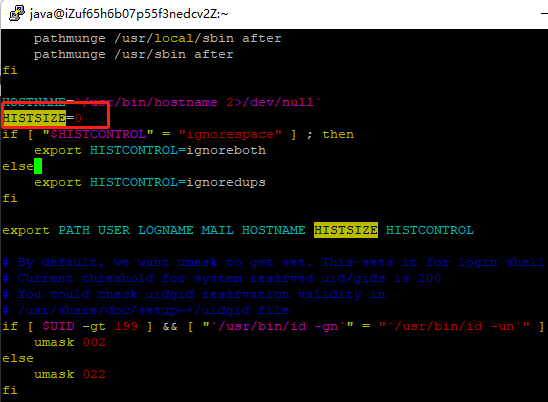
3.3 清除有敏感数据的存储空间
通过sudo vim /etc/profile打开配置文件,将HISTSIZE设置为0:
Comments NOTHING